
“Missed package?” Scam fooling thousands
Package delivery scams are relentless, and no longer focus on shopping seasons and Christmas. NZ Post delivered more than 81.9 million courier parcels in the 12 months to 1 April 2024. Many Kiwis get too many packages to keep track of, and that's exactly what scammers are counting on.
Delivery scams are evolving, and these days they can appear quite subtle. Look for these signs:
- Unprofessional layout and missing shipment details - The email design is sloppy, and key information like a real pickup address and customer account number is missing — not what you'd expect from DHL or NZ Post.
- Suspicious email and links - Only an email address is shown (no real address), and the tracking link could redirect you to a phishing site.
- Urgent, pressuring language - The email tries to rush you into clicking quickly — classic tactic scammers use to trick people.
- Custom payment requests – Even if it's just a small 'customs' fee, be cautious. New Zealand Customs does not contact individuals or businesses about paying customs duty. Imported goods are handled by licensed freight forwarders, not by NZ Customs.
Below is an example.
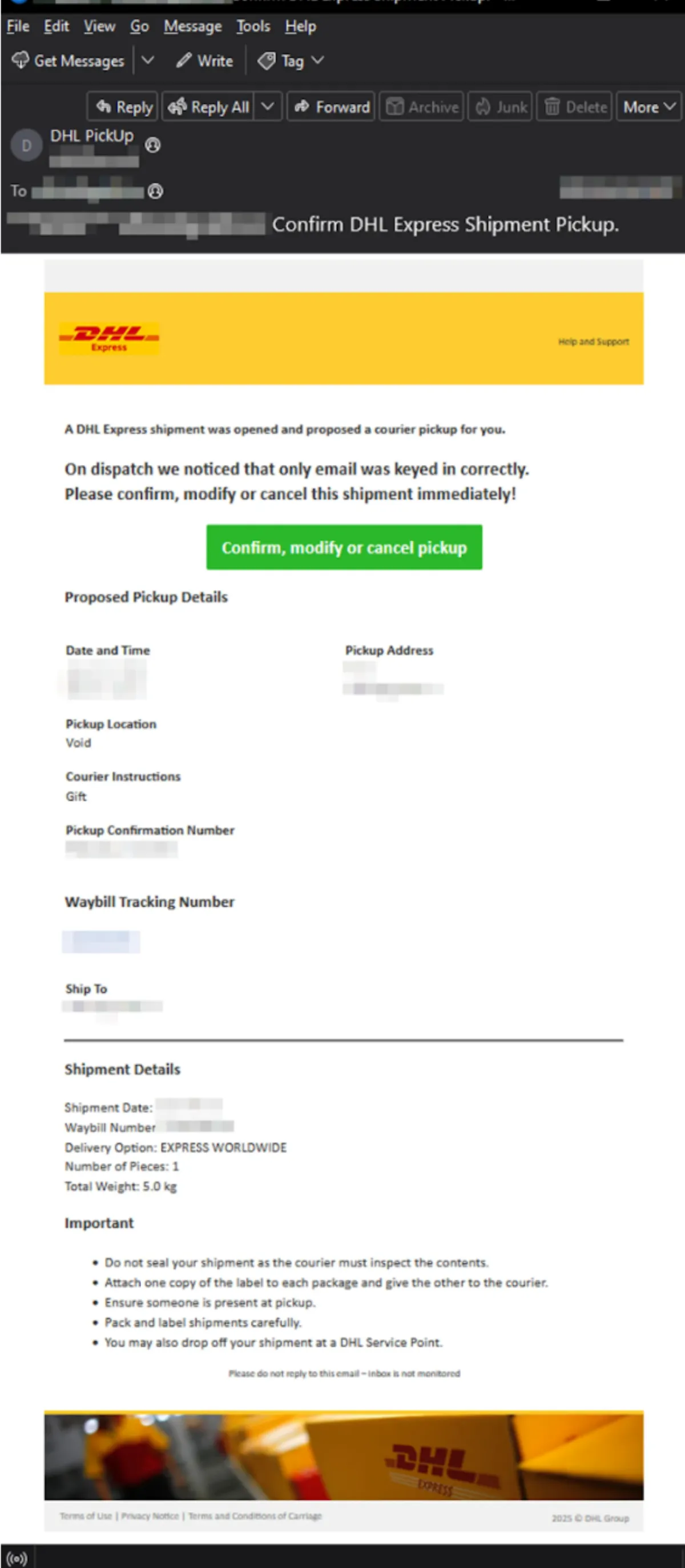
The email doesn't stand out particularly at first glance. And that's exactly why this example is so interesting: it strikes a balance between appearing legitimate and hiding the usual red flags often found in scam emails. One quick trick to check if an email is fake is to look at the sender's address. Does it really come from DHL or something odd like info@ioxr.art?
Looking further into the email body, there's a button that clearly encourages the user to click and proceed. It's designed to appear as though it will take the recipient to DHL's official tracking page.
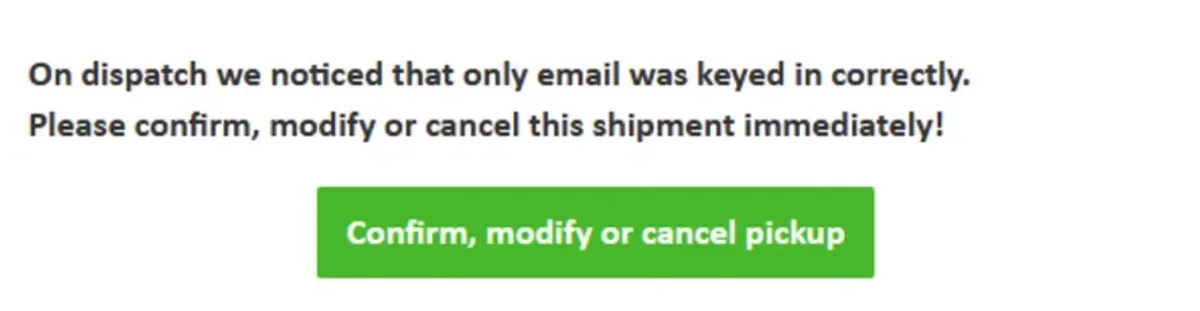
The link actually goes to a site hosted on IPFS — a system that makes it hard to take things down, which is exactly why scammers love it. While this makes it harder to take malicious content offline, it also raises a red flag — this is not where you'd expect a legitimate DHL email to direct you.
Since IPFS is compatible with modern browsers, it opens a landing page. The page doesn't display much information at all, but it personalises the scam by pre-filling the login field with the recipient's email address. That's a subtle but clever touch — it adds just enough legitimacy to convince some users to proceed.
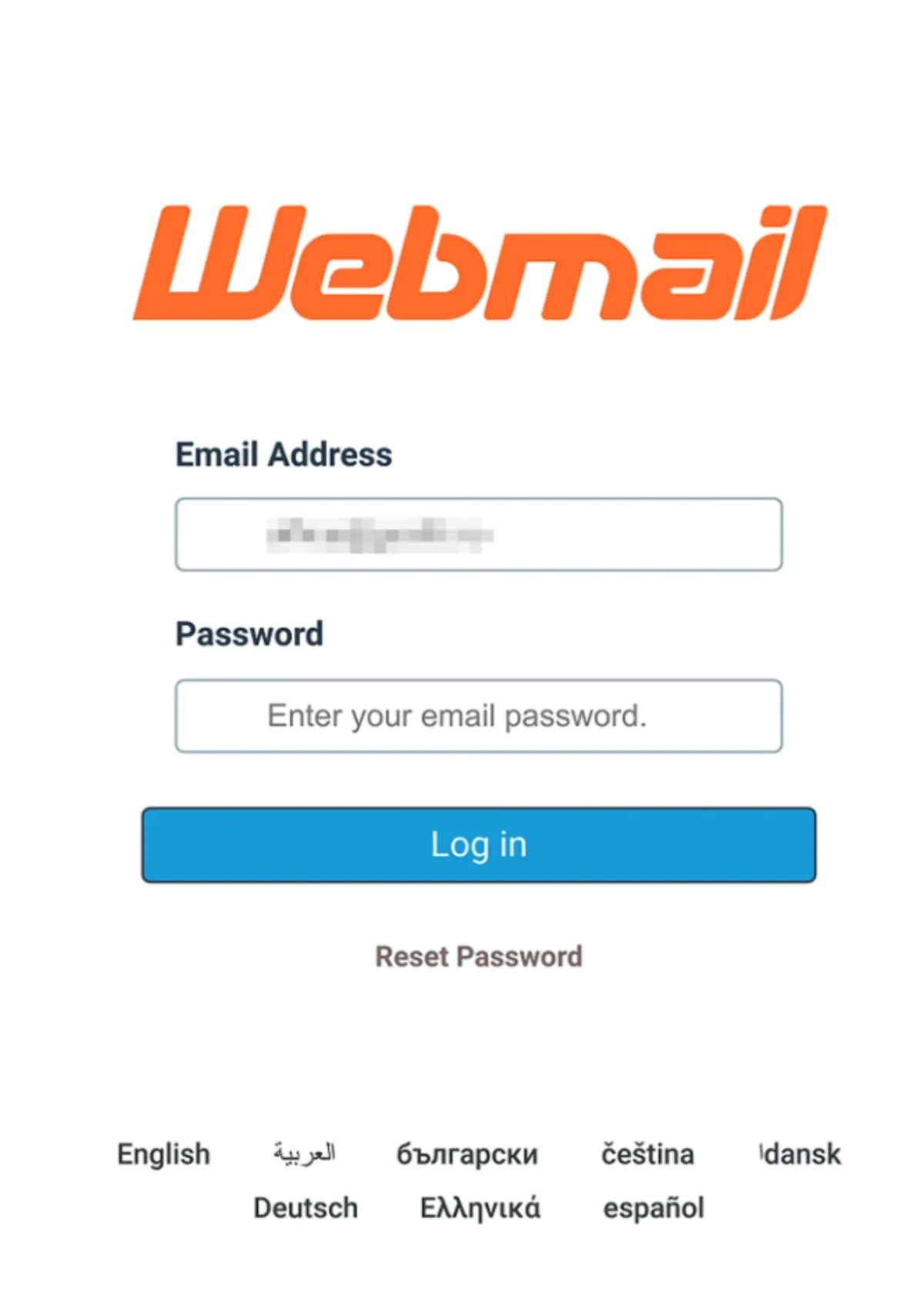
The site even blocks right-clicking so you can't inspect the code — a common trick scammers use to hide what they're really doing.

The language selection links at the bottom are non-functional — clicking them does nothing. But most users won't bother to test those, so they serve a purely visual purpose: to make the site look more legitimate and avoid raising suspicion.
At first glance, most of the code is dedicated to CSS styling — which is unusual, as this would typically be loaded from external files. Embedding so much CSS directly into the page is a strange choice and already raises some suspicion. But beyond the formatting, there are several indicators that strongly suggest this is a phishing site.
- The URL points to IPFS storage (ipfs.io): Real login portals (e.g., for Microsoft, Google, etc.) use official domains (like microsoft.com, google.com, outlook.com). ipfs.io is a decentralised file storage system — no legitimate organisation will host login pages there.
- Form captures email and password with no backend: The form fields (email, password) do not submit anywhere obvious. Real login forms send credentials securely (HTTPS POST) to legitimate servers. Phishing forms either harvest the info silently or submit it to hidden malicious endpoints.
- Mix of languages links with no functionality: There are fake "language links" (Arabic, Czech, Danish, etc.) all pointing to the same broken IPFS page. On real sites, language selectors actually change the content dynamically.
- Poor HTML/CSS quality and broken elements: The code is poorly formatted, has broken inline styles, and excessive base64-encoded images. Real corporate web pages are carefully coded, fully polished, and use proper asset management (e.g., not massive inline blobs).
The distribution of this scam shows New Zealand and Australia are real targets.
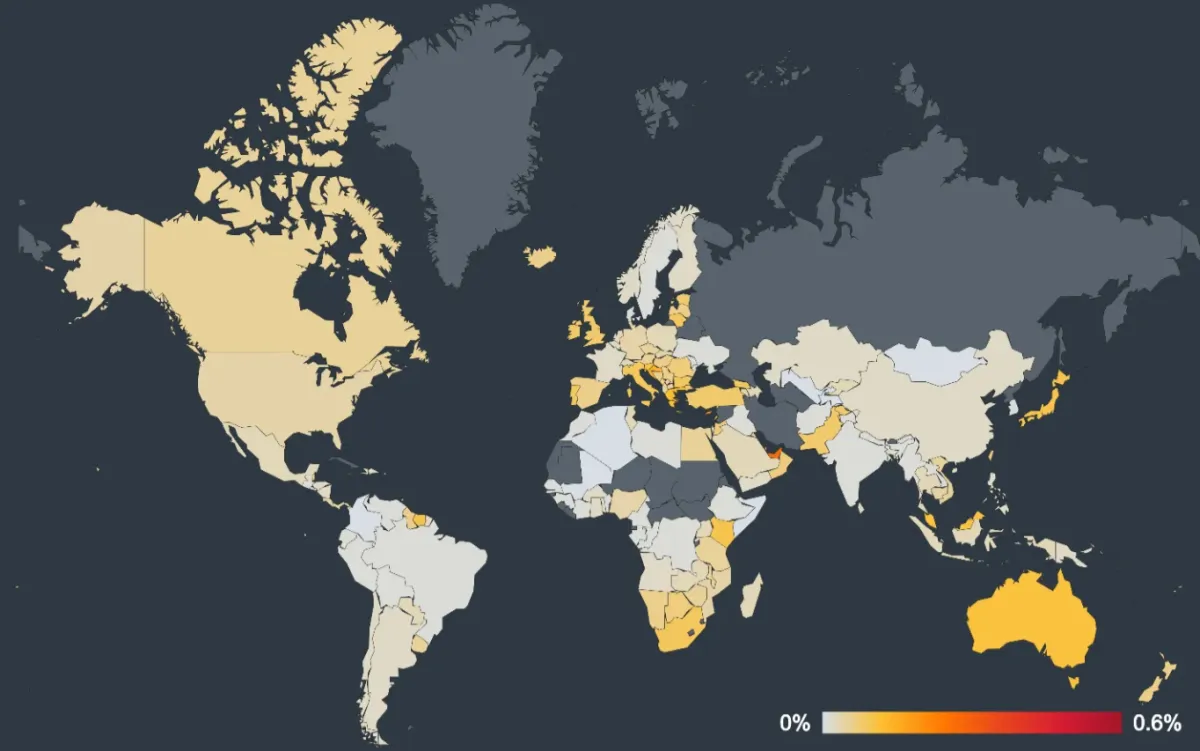
Due to the generic nature of the landing page and the broad appeal of the phishing message, this scam can be deployed almost identically worldwide. This increases the attackers' chances of success by allowing them to trick users in multiple regions into handing over their credentials — which can then be repurposed for more targeted, high-value attacks.
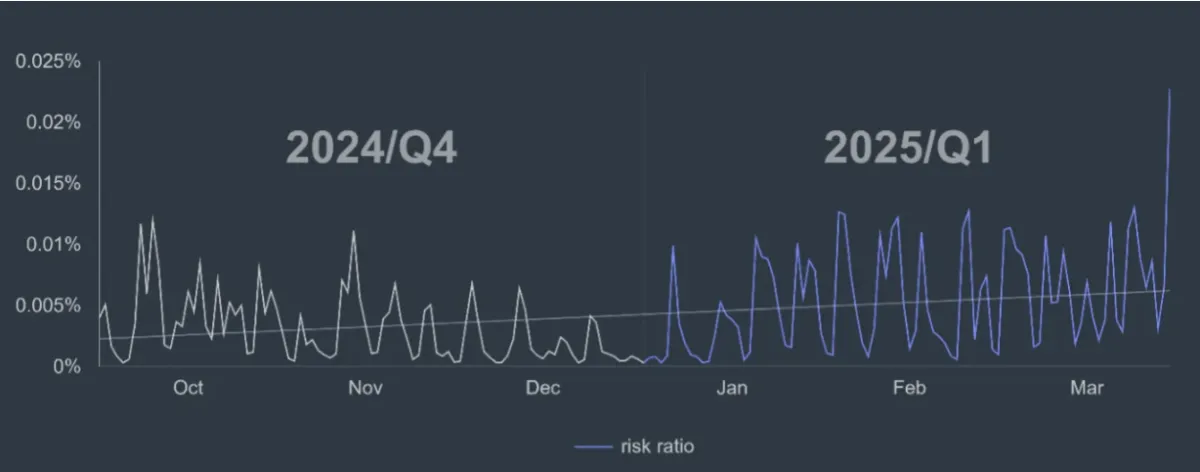
The threat is steadily increasing. The dips visible in the data typically correspond to weekends, suggesting that the most successful day to launch an attack is Monday — when people return to full inboxes and are still easing into the workweek. Aside from this pattern, the threat remains consistent and persistent. Gen Digital cybersecurity experts fully expect this scam, or variations of it, to continue appearing now and in the foreseeable future.
Kiwis can protect themselves against these scams in five easy ways:
- Always check the email headers
Look at the sender's email address closely — is it from a legitimate domain you recognise? Official companies will never use suspicious or unfamiliar domains. - Examine the landing page
Does the page look like what you expected? If something feels off, it probably is. Be especially wary if you're redirected to an unfamiliar URL. - Assess the design and formatting
Most phishing emails are poorly designed. Look for inconsistent fonts, low-quality logos, or broken elements that a professional company would never send. - Watch for time pressure and manipulative language
Scammers often create a false sense of urgency — claiming your package will be returned or your account will be locked unless you act immediately. Take a moment to verify before clicking. - Do not share sensitive information
Never give out personal or financial details in response to suspicious messages.
Email scams aren't going away, but staying alert can keep you safe. Before you click, take a breath, check the sender, and when in doubt, go straight to the company's official website.

